A slight glitch?
Page 5 - Passionate about caravans & motorhome? Join our community to share that passion with a global audience!
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Jun 16, 2020
- 5,880
- 2,785
- 17,935
But not 100%. Remember, you had some from my old compromised email address a few years ago. Probably because it recognised it as a ‘safe’. Address.We are registered with www.pobox.com and pay them about £18 a year. They stop spam at source and on the basic account you can have three email addresses with them. You can continue to use existing email address and all emails are directed to your existing email address. We have been using them for over25 years.
John
- Jul 18, 2017
- 16,925
- 5,504
- 50,935
There is nothing you can do about that sort of email as it is not recognised as spam by any anti-spam app.But not 100%. Remember, you had some from my old compromised email address a few years ago. Probably because it recognised it as a ‘safe’. Address.
John
Why not simply block a known "old compromised email address"?There is nothing you can do about that sort of email as it is not recognised as spam by any anti-spam app.
By inference, being "old", it can't be coming from the genuine source?
- Jul 18, 2017
- 16,925
- 5,504
- 50,935
You cannot block it until it has been received. Not an easy one for find a solution as you may end up blocking your friend's genuine email address. Can't remember how they do it, but the email address looks genuine but does not come from the friend's address.Why not simply block a known "old compromised email address", it can't be coming from the genuine source?
A couple of years ago, in addition to John's email address being compromised numerous members of our regiment had the same issue. Generally the email stated that they had been robbed, lost their wallet etc and needed money to get home.
- Nov 11, 2009
- 25,890
- 9,554
- 50,935
You press on the email address and it reveals the originator. That tells you instantly if it’s a contact or one you don’t want. Then when it’s highlighted you get an option to block it.You cannot block it until it has been received. Not an easy one for find a solution as you may end up blocking your friend's genuine email address. Can't remember how they do it, but the email address looks genuine but does not come from the friend's address.
A couple of years ago, in addition to John's email address being compromised numerous members of our regiment had the same issue. Generally the email stated that they had been robbed, lost their wallet etc and needed money to get home.
- Jul 18, 2017
- 16,925
- 5,504
- 50,935
Thanks I am well aware of the above however the email address is the genuine address which is the problem. In the email you are asked to help by forwarding on some money to "X" at an address. The amounts are small so as not to create any suspicion.You press on the email address and it reveals the originator. That tells you instantly if it’s a contact or one you don’t want. Then when it’s highlighted you get an option to block it.
- Jan 3, 2012
- 11,265
- 2,664
- 40,935
Thanks for information very usefulWe are registered with www.pobox.com and pay them about £18 a year. They stop spam at source and on the basic account you can have three email addresses with them. You can continue to use existing email address and all emails are directed to your existing email address. We have been using them for over25 years.
Spam is generally classed as 'unsolicited emails' but I think there are at least two classes within that. Emails that are scams and emails that are marketing junk. From talking to many of my friends is clear that the latter is what fills up their inboxes, to the extent that one friend rarely uses email now because its full of junk and hard to spot the genuine emails.
Too many of these people are not aware of what they are signing up for when buying stuff on line or browsing web sites that collect your information. As a result they get sent junk they don't want and they're not even aware that many emails have an unsubscribe link at the bottom.
Some less scrupulous companies will automatically opt you in and make it hard to opt out.
So beware of what you're clicking on or signing up to.
Companies like Google, Apple and Microsoft are pretty good at filtering out the scam spam. I have my own domain and the hosting company is very good at this and makes it easy to block persistent offenders if they slip through.
In the end we are all responsible for our own on line actions.
Too many of these people are not aware of what they are signing up for when buying stuff on line or browsing web sites that collect your information. As a result they get sent junk they don't want and they're not even aware that many emails have an unsubscribe link at the bottom.
Some less scrupulous companies will automatically opt you in and make it hard to opt out.
So beware of what you're clicking on or signing up to.
Companies like Google, Apple and Microsoft are pretty good at filtering out the scam spam. I have my own domain and the hosting company is very good at this and makes it easy to block persistent offenders if they slip through.
In the end we are all responsible for our own on line actions.
- Jul 18, 2017
- 16,925
- 5,504
- 50,935
I avoid clicking on links in emails preferring to Google and then enter the website that way and even then it is not 100% safe. Secondly I generally use my CC via Paypal to make a purchase Online even if the value of the goods is less than £100.Spam is generally classed as 'unsolicited emails' but I think there are at least two classes within that. Emails that are scams and emails that are marketing junk. From talking to many of my friends is clear that the latter is what fills up their inboxes, to the extent that one friend rarely uses email now because its full of junk and hard to spot the genuine emails.
Too many of these people are not aware of what they are signing up for when buying stuff on line or browsing web sites that collect your information. As a result they get sent junk they don't want and they're not even aware that many emails have an unsubscribe link at the bottom.
Some less scrupulous companies will automatically opt you in and make it hard to opt out.
So beware of what you're clicking on or signing up to.
Companies like Google, Apple and Microsoft are pretty good at filtering out the scam spam. I have my own domain and the hosting company is very good at this and makes it easy to block persistent offenders if they slip through.
In the end we are all responsible for our own on line actions.
Today I got an email from Mhlengi Gwala a person we helped 4 years ago. Circumstances were that he was a potential class athlete and while riding his bicycle in Durban he was attacked by two individuals and they use a hacksaw to cut off one of his legs.
We knew it was genuine and did a donation to the Gofundme to help him get a prosthetic leg. This new email contained numerous links which I will not click on as they are asking for further donation to help fund a high-performance bike.
Rather they clicking on the links, we will go straight to the site to check if it is genuine and take it from there. Look up his name as he is a world class athlete.
- Jun 16, 2020
- 5,880
- 2,785
- 17,935
The friends you describe remind me of how my old email address was. It happened for the reasons you describe. My new address’s are completly spam free. Mainly, I believe this is because I am far more careful with who I pass it onto.Spam is generally classed as 'unsolicited emails' but I think there are at least two classes within that. Emails that are scams and emails that are marketing junk. From talking to many of my friends is clear that the latter is what fills up their inboxes, to the extent that one friend rarely uses email now because its full of junk and hard to spot the genuine emails.
Too many of these people are not aware of what they are signing up for when buying stuff on line or browsing web sites that collect your information. As a result they get sent junk they don't want and they're not even aware that many emails have an unsubscribe link at the bottom.
Some less scrupulous companies will automatically opt you in and make it hard to opt out.
So beware of what you're clicking on or signing up to.
Companies like Google, Apple and Microsoft are pretty good at filtering out the scam spam. I have my own domain and the hosting company is very good at this and makes it easy to block persistent offenders if they slip through.
In the end we are all responsible for our own on line actions.
It may also be the case that companies are far more aware of their own security and how the handle customers information.
Getting rid of my old compromised email address was not easy. It was used as a username with many organisations. As well as my contact details. It was easy to write to all of my contacts and ask them to delete my old address and update with the new one. But only about half actually did it. Months later, contacts would write to me to tell me they had recieved a spam mail ostensibly from me. I had to politly remind them that I had asked them to delete it. I needed to monitor it for a couple of years.
The other mistake I made in my ignorance was to use the address provided by my internet supplier. This ties you into that supplier. Much better to use free addresses like Gmail, which can move with you.
I made the same mistake when I moved to Apple. But as I am happy to stay with them. I am not too bothered.
John
- Nov 11, 2009
- 25,890
- 9,554
- 50,935
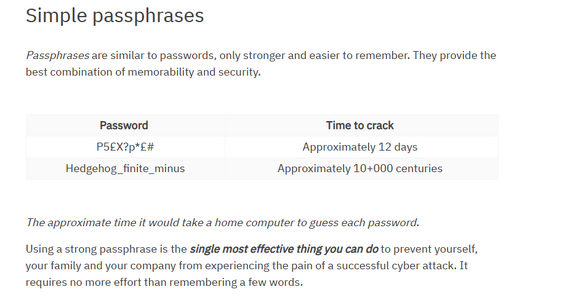
That's an interesting post and my Router has a very easy to remember Pass Phrase even though I don't require it very often. Do you know how the cracking time for a Pass Phrase compares to the cracking time for the Apple generated long passwords with their array of Characters, Symbols and Numerics?On the subject of passwords, passphrases are far more secure, and add a number and special character even more so
View attachment 6110View attachment 6110
- Nov 11, 2009
- 25,890
- 9,554
- 50,935
I have a similar issue with an Email address that I have had since 2006 and it's quite a chore to exit it. But I have one "best address" that is reserved for friends and reputable contacts IE NHS, banks etc. I have recently craeted another Yahoo mail address which will be the one that I use for purchases and run of the mill stuff. My Hotmail address will attract up to 30-40 junk mails per day, but it takes a minute to scan down and Bin those that I don't want. Any remaining ones stay in Junk until I have looked at them. Some may have been Junked incorrectly so I go into Hotmail and put the setting to ensure future ones go into Inbox.The friends you describe remind me of how my old email address was. It happened for the reasons you describe. My new address’s are completly spam free. Mainly, I believe this is because I am far more careful with who I pass it onto.
It may also be the case that companies are far more aware of their own security and how the handle customers information.
Getting rid of my old compromised email address was not easy. It was used as a username with many organisations. As well as my contact details. It was easy to write to all of my contacts and ask them to delete my old address and update with the new one. But only about half actually did it. Months later, contacts would write to me to tell me they had recieved a spam mail ostensibly from me. I had to politly remind them that I had asked them to delete it. I needed to monitor it for a couple of years.
The other mistake I made in my ignorance was to use the address provided by my internet supplier. This ties you into that supplier. Much better to use free addresses like Gmail, which can move with you.
I made the same mistake when I moved to Apple. But as I am happy to stay with them. I am not too bothered.
John
- Jul 18, 2017
- 16,925
- 5,504
- 50,935
Not sure how one is supposed to remember long passwords with an array of characters, symbols and numerics? Struggle to remember names and phone numbers. LOL!That's an interesting post and my Router has a very easy to remember Pass Phrase even though I don't require it very often. Do you know how the cracking time for a Pass Phrase compares to the cracking time for the Apple generated long passwords with their array of Characters, Symbols and Numerics?
- Nov 11, 2009
- 25,890
- 9,554
- 50,935
You don't remember them as they are held in the Browser or a Password Manager. If required you can always access them. But they will be used and inserted by fingerprint ID or facial recognition ID, or if on my computer by cursor.Not sure how one is supposed to remember long passwords with an array of characters, symbols and numerics? Struggle to remember names and phone numbers. LOL!
- Jul 18, 2017
- 16,925
- 5,504
- 50,935
You don't remember them as they are held in the Browser or a Password Manager. If required you can always access them. But they will be used and inserted by fingerprint ID or facial recognition ID, or if on my computer by cursor.
If they are held in the browser surely that compromises security? If they are inserted when you click on the password block and they are inserted, surely there is no point as anyone could do the same? Apologies if I have misunderstood.
Currently I do keep a record of passwords that i use for various sites on my laptop. However I use a code that I understand to allocate them to the correct website. Many sites will keep your login details including password even if you delete all the cookies and clear your cache.
Only passwords kept in my head are those for our bank, Paypal and CC who also require a verification code.
- Jul 19, 2021
- 615
- 426
- 5,135
sorry I don't. I have as little to do with Apple as possibleThat's an interesting post and my Router has a very easy to remember Pass Phrase even though I don't require it very often. Do you know how the cracking time for a Pass Phrase compares to the cracking time for the Apple generated long passwords with their array of Characters, Symbols and Numerics?
- Nov 11, 2009
- 25,890
- 9,554
- 50,935
Who is going to use my home computer to access passwords? It shuts down after five minutes of non use and requires me to insert my admin password which has to be done using the keyboard. even then bank, credit card Amazon, Paypal etc are not held on it as I remember those and input manually.If they are held in the browser surely that compromises security? If they are inserted when you click on the password block and they are inserted, surely there is no point as anyone could do the same? Apologies if I have misunderstood.
Currently I do keep a record of passwords that i use for various sites on my laptop. However I use a code that I understand to allocate them to the correct website. Many sites will keep your login details including password even if you delete all the cookies and clear your cache.
Only passwords kept in my head are those for our bank, Paypal and CC who also require a verification code.
- Jul 18, 2017
- 16,925
- 5,504
- 50,935
I take my laptop away with me when out in the caravan, but if you leave yours at home then no issue unless you have a burglar.Who is going to use my home computer to access passwords? It shuts down after five minutes of non use and requires me to insert my admin password which has to be done using the keyboard. even then bank, credit card Amazon, Paypal etc are not held on it as I remember those and input manually.
- Nov 11, 2009
- 25,890
- 9,554
- 50,935
A burglar would still need to input my admin password to the MAC MINI or steal it and try and gain access. But as I say I don't keep "key finance" passwords on the computer I remember them. And even if the burglar managed to access the computer it still need access permission for passwords stored in Safari. My phone and iPad leave the house.I take my laptop away with me when out in the caravan, but if you leave yours at home then no issue unless you have a burglar.
I take my laptop away with me when out in the caravan, but if you leave yours at home then no issue unless you have a burglar.
If Windows 11 or 10 then there might be the biometric sign in, Windows Hello, face via the probably inbuilt webcam, or on some laptops fingerprint reader.
That coupled with a lengthy user password, the chances of the burglar looking alike enough to any of us is "rare".
LINKI
As said earlier just keep to using an encrypted USB stick, none of my computers etc holding in any form my critical passwords, or so I hope, not knowing for certain what these days is being "watched".
I can see real issues I would have if trying to access my bank accounts on a PC, if in a location without a messaging viable mobile phone link; all are solidly linked to requiring secondary verification.
Last edited:
- Jun 16, 2020
- 5,880
- 2,785
- 17,935
V9tPfqK-WC"G0,3n+$}Jl3PM#R=yP-l%
This is a typical password generated by my password manager. I certainly do not remember them. To use it I just need access to the vault. The password for this I have hidden in my files. But in normal use, it opens with facial recognition. Easy and quick.
My bank account opens almost instantly. On two phones and two iPads. And I believe the security is excellent.
Same with paying using my phone. Just two clicks, show my face and pay.
I understand that lots of people are very nervous about taking such a plunge, but the banks are happy with the security provided.
John
This is a typical password generated by my password manager. I certainly do not remember them. To use it I just need access to the vault. The password for this I have hidden in my files. But in normal use, it opens with facial recognition. Easy and quick.
My bank account opens almost instantly. On two phones and two iPads. And I believe the security is excellent.
Same with paying using my phone. Just two clicks, show my face and pay.
I understand that lots of people are very nervous about taking such a plunge, but the banks are happy with the security provided.
John
What happens with Lasting Power of Attorney (LPA) which can be set up to allow the nominated attorneys to handle financial matters during permanent disability or temporary disability - use a photo of the account holder to gain access?V9tPfqK-WC"G0,3n+$}Jl3PM#R=yP-l%
This is a typical password generated by my password manager. I certainly do not remember them. To use it I just need access to the vault. The password for this I have hidden in my files. But in normal use, it opens with facial recognition. Easy and quick.
My bank account opens almost instantly. On two phones and two iPads. And I believe the security is excellent.
Same with paying using my phone. Just two clicks, show my face and pay.
I understand that lots of people are very nervous about taking such a plunge, but the banks are happy with the security provided.
John
- Nov 11, 2009
- 25,890
- 9,554
- 50,935
No, you can arrange access to a Donors accounts with the banks, building societies etc.by discussion as different companies use different access requirements. For my BIL’s accounts I can use telephone banking where my voice is my my password, traditional usernames with passwords, some being accessed by passwords stored in Safari with fingerprint ID, or just plain old fashioned go into the office with ID. All have two stage verification as a minimum.What happens with Lasting Power of Attorney (LPA) which can be set up to allow the nominated attorneys to handle financial matters during permanent disability or temporary disability - use a photo of the account holder to gain access?
TRENDING THREADS
-
-
-
Mandatory eye tests for drivers over 70 being proposed by HMG. Good or bad?
- Started by Dustydog
- Replies: 182
-
-
-
Caravan Battery we think is dead even though we have solar
- Started by Saxo Appeal
- Replies: 169
-

Practical Caravan is part of Future plc, an international media group and leading digital publisher. Visit our corporate site.
© Future Publishing Limited Quay House, The Ambury, Bath BA1 1UA. All rights reserved. England and Wales company registration number 2008885.